ISO 27001 for SaaS companies
ISO/IEC 27001 is the international standard for building an Information Security Management System (ISMS). It defines what a strong security program needs to cover, without dictating how you should run your business.
The standard is risk-driven by design: you set scope, identify threats, choose controls, and continuously improve. That means SaaS companies can tailor ISO 27001 to their stack and workflows instead of bending to generic checklists. The latest revision is ISO/IEC 27001:2022 (official standard).
Why it matters
Confidence for enterprise prospects and security questionnaires.
Clear ownership across engineering, product, and leadership.
A repeatable rhythm for managing risks, vendors, and incidents.
Proof that security is intentional, measurable, and improving.
The ISO 27000 family
ISO 27001 sits within a broader family. Key ones to know:
- ISO/IEC 27000 Overview and vocabulary.
- ISO/IEC 27001 ISMS requirements (certifiable).
- ISO/IEC 27002 Control guidance.
- ISO/IEC 27003 Implementation guidance.
- ISO/IEC 27004 Measurement and metrics.
- ISO/IEC 27005 Risk management guidance.
- ISO/IEC 27017 / 27018 Cloud security and PII in public cloud.
- ISO/IEC 27701 Privacy extension to ISO 27001.
There are more specialized standards (auditing, supplier security, etc.), but these are the ones SaaS teams most often encounter.
How ISO 27001 is structured
An ISMS aligns people, processes, and technology so security is intentional, not accidental. ISO 27001 is built on continuous improvement (Plan-Do-Check-Act), which means your security posture evolves with your product and customer base instead of being a one-time project.
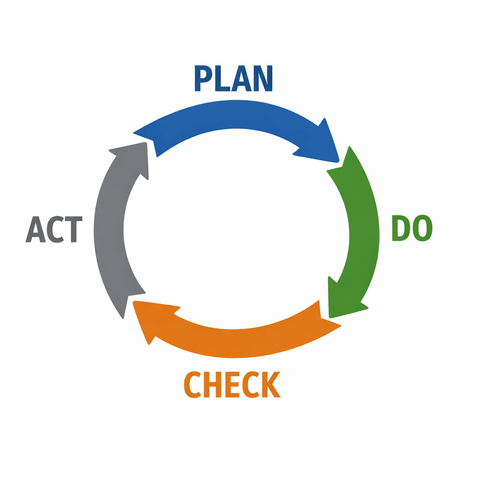
Define scope, risks, and controls.
Implement controls and ways of working.
Measure, audit, and review performance.
Improve and refine based on insights.
We translate the requirements into everyday SaaS practices: secure development workflows, cloud configuration baselines, vendor onboarding, incident readiness, and evidence that stands up in audits.
For growth-stage teams, we keep the documentation lightweight, automate evidence where possible, and plug into the tools you already use (ticketing, repos, CI/CD, cloud).
Core clauses (high level)
ISO 27001 includes clauses that define how you scope, run, and improve your ISMS.
Define business context, interested parties, and the ISMS scope boundaries and interfaces.
Demonstrate leadership commitment, set security policy, and assign clear roles and responsibilities.
Set objectives, assess and treat risks, and plan changes to the ISMS.
Provide people, competence, awareness, resources, and controlled documented information.
Operate controls in practice, manage changes, and oversee suppliers and outsourced processes.
Monitor and measure performance, run internal audits, and hold management reviews.
Handle nonconformities, take corrective action, and continuously improve the ISMS.
Annex A (93 controls)
Annex A lists security controls you select based on your risks. You can exclude controls if you document the rationale.
Policies, roles, secure development, supplier due diligence.
Onboarding, access lifecycle, awareness.
Workspace and device protections.
Identity, logging, encryption, backups, continuity.
How we help
Pick what you need: hands-on implementation, an independent internal auditor, or ongoing fractional CISO (virtual CISO) leadership to keep your ISMS running smoothly.
Build and launch your ISMS
For SaaS companies that want guidance, templates, and hands-on support.
- Gap assessment, scope definition, and risk register setup.
- Policy set tailored to your cloud stack and SDLC.
- Evidence collection playbook and automation where possible.
- Coaching for leadership, engineers, and product owners.
Stay audit-ready
For certified or in-flight teams that need an independent internal auditor.
- Audit program planning and sampling of controls and evidence.
- Findings with clear remediation actions and owners.
- Certification prep: readiness checks, stakeholder interviews, evidence review.
- Reports you can share with management and external auditors.
Ongoing security leadership
For teams that need a security lead to keep ISO 27001 aligned with growth.
- Security roadmap, risk ownership, and policy upkeep.
- Management reviews, metrics, and evidence hygiene.
- Vendor reviews, incident readiness, and stakeholder reporting.
- Bridge between engineering, product, and leadership.
Ready to make ISO 27001 work for your SaaS?
Tell us where you are today, whether it's a first audit coming up, sales blockages, or rebuilding after growth. We will tailor the approach and keep the process light.